Nordkorea misstänks ligga bakom Wannacry
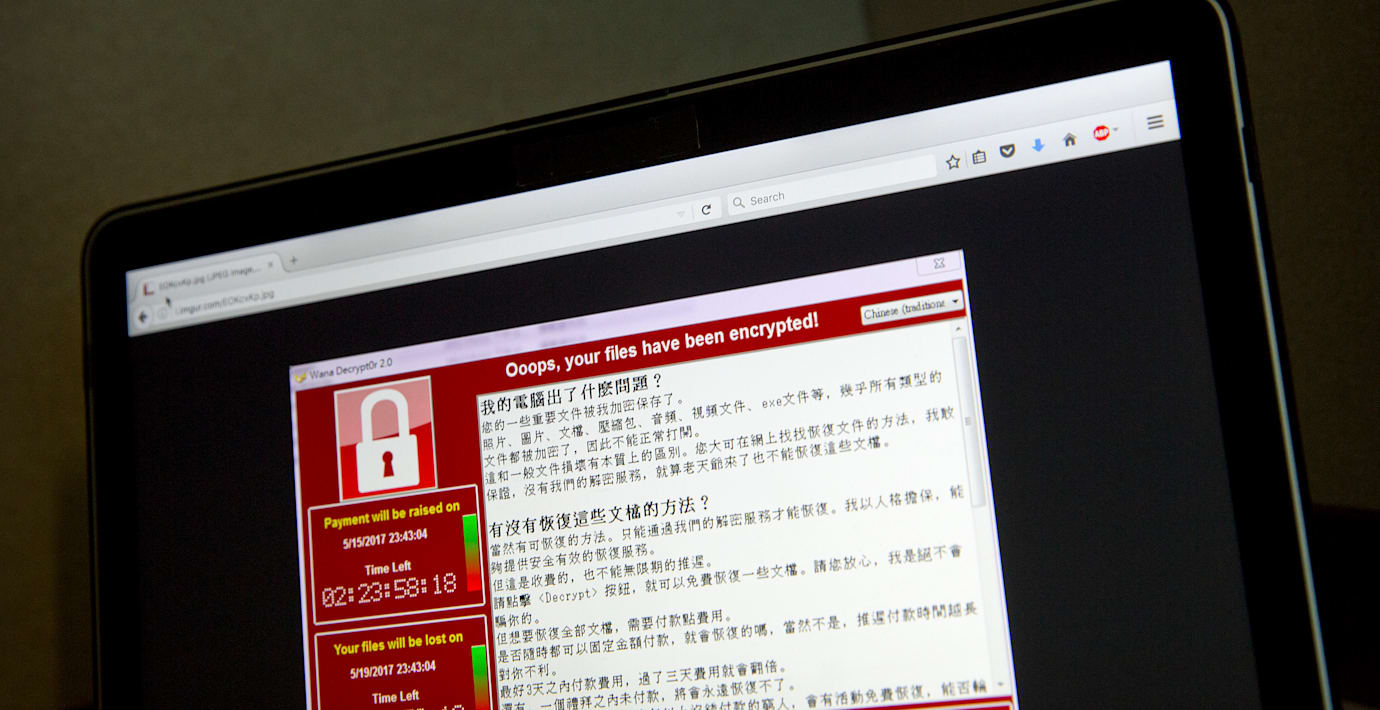
Hackerattacken Wannacry som drabbade ett stort antal myndigheter och företag världen över kan ha kommit från Nordkorea, rapporterar BBC och Washington Post.
Storbritanniens cybersäkerhetscenter NCSC har lett den internationella utredningen av attacken. Källor säger till BBC att NCSC tror att en hackergrupp som är känd som Lazarus, som tidigare kopplats till Nordkorea, lanserade attacken.
Samma grupp misstänks ligga bakom en attack mot Sony 2014 och bedrägerier riktade mot banker. Storbritanniens offentliga sjukvård NHS drabbades hårt av attacken i maj.
bakgrund
Lazarus
Wikipedia (en)
Lazarus Group is a cybercrime group made up of an unknown number of individuals. While not much is known about the Lazarus Group, researchers have attributed many cyber attacks to them over the last decade.
bakgrund
Wannacry
Wikipedia (en)
The WannaCry ransomware attack was a worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency.
The attack began on Friday, 12 May 2017, and within a day was reported to have infected more than 230,000 computers in over 150 countries. Parts of Britain's National Health Service (NHS), Spain's Telefónica, FedEx and Deutsche Bahn were hit, along with many other countries and companies worldwide. Shortly after the attack began, Marcus Hutchins, a 22 year-old web security researcher from North Devon in England, who blogs as "MalwareTech", discovered an effective kill switch by registering a domain name he found in the code of the ransomware. This greatly slowed the spread of the infection, effectively halting the initial outbreak on Monday, 15 May 2017, but new versions have since been detected that lack the kill switch. Researchers have also found ways to recover data from infected machines under some circumstances.
WannaCry propagates using EternalBlue, an exploit of Windows' Server Message Block (SMB) protocol. Much of the attention and comment around the event was occasioned by the fact that the U.S. National Security Agency (NSA) had discovered the vulnerability in the past, but used it to create an exploit for its own offensive work, rather than report it to Microsoft. It was only when the existence of this vulnerability was revealed by The Shadow Brokers that Microsoft became aware of the issue, and issued a "critical" security patch on 14 March 2017 to remove the underlying vulnerability on supported versions of Windows, though many organizations had not yet applied it.
Those still running older, unsupported versions of Microsoft Windows, such as Windows XP and Windows Server 2003, were initially at particular risk, but Microsoft released an emergency security patch for these platforms as well. Almost all victims of the cyberattack were running Windows 7, prompting a security researcher to argue that its effects on Windows XP users were "insignificant" in comparison.
Within four days of the initial outbreak, security experts were saying that most organizations had applied updates, and that new infections had slowed to a trickle. WannaCry is the ransomware computer worm that targets computers running Microsoft Windows. Initially, the worm uses the EternalBlue exploit to enter a computer, taking advantage of a vulnerability in Microsoft's implementation of the Server Message Block (SMB) protocol. It installs DoublePulsar, a backdoor implant tool, which then transfers and runs the WannaCry ransomware package.
Several organizations have released detailed technical writeups of the malware, including Microsoft, Cisco, Malwarebytes, Symantec and McAfee.
The "payload" works in the same fashion as most modern ransomware: it finds and encrypts a range of data files, then displays a "ransom note" informing the user and demanding a payment in bitcoin. It is considered a network worm because it also includes a "transport" mechanism to automatically spread itself. This transport code scans for vulnerable systems, then uses the EternalBlue exploit to gain access, and the DoublePulsar tool to install and execute a copy of itself.
Omni är politiskt obundna och oberoende. Vi strävar efter att ge fler perspektiv på nyheterna. Har du frågor eller synpunkter kring vår rapportering? Kontakta redaktionen