Wannacry-attacken lyfte Blackberry-aktien
Efter den stora hackerattacken Wannacry i maj har den tidigare mobiltillverkaren Blackberry åter hamnat i rampljuset. Den här gången för sina satsningar på it-säkerhet, skriver Reuters.
Aktien lyfte nära 9 procent på Torontobörsen i går. Företaget ägnar sig också åt mjukvara för fordon – och på senare tid har förutsättningarna för god försäljning för den ökat.
bakgrund
Wannacry
Wikipedia (en)
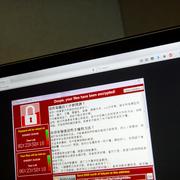
The WannaCry ransomware attack was a worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency.
The attack started on Friday, 12 May 2017, and within a day was reported to have infected more than 230,000 computers in over 150 countries. Parts of Britain's National Health Service (NHS), Spain's Telefónica, FedEx and Deutsche Bahn were hit, along with many other countries and companies worldwide.
WannaCry spreads across local networks and the Internet to systems that have not been updated with recent security updates, to directly infect any exposed systems. A "critical" patch had been issued by Microsoft on 14 March 2017 to remove the underlying vulnerability for supported systems, nearly two months before the attack, but many organizations had not yet applied it. Those still running exposed older, unsupported operating systems such as Windows XP and Windows Server 2003, were initially at particular risk but the day after the outbreak Microsoft took the unusual step of releasing updates for these operating systems too. Almost all victims are running Windows 7 or newer.
Much of the attention and comment around the event was occasioned by the fact that the U.S. National Security Agency (NSA) had discovered the vulnerability in the past, but instead of informing Microsoft had built the EternalBlue exploit for their own offensive work. It was only when the existence of this was revealed by The Shadow Brokers that Microsoft became aware of the issue, and could produce a security update.
Shortly after the attack began, a web security researcher who blogs as "MalwareTech" discovered an effective kill switch by registering a domain name he found in the code of the ransomware. This greatly slowed the spread of the infection, but new versions have since been detected that lack the kill switch.
Within four days of the initial outbreak, security experts were saying that most organizations had applied updates, and that new infections had slowed to a trickle. Researchers are starting to find ways to recover data from infected machines.
Omni är politiskt obundna och oberoende. Vi strävar efter att ge fler perspektiv på nyheterna. Har du frågor eller synpunkter kring vår rapportering? Kontakta redaktionen